
Security, like safety, is a top priority for the aviation industry, and is embedded in all operations. That’s why it’s critical to manage it properly.
Threats to aviation continue to evolve. Airlines, airports, governments, international agencies and independent aviation stakeholders are striving to enhance and develop aviation security capabilities. The importance of incident management, collaboration and security assurance should not be compromised. The industry needs to continually adapt to ever-changing regulations and challenges that the global security environment presents as they look to expand and evolve their operations.
Strengthened security is always an asset, however amidst this, it can also improve operational efficiencies within your organization, improve the relationship between airports, airlines and aviation authorities as well as enhance customer satisfaction.
Take the five-minute SeMS Evaluation Test to learn more.
The basis for aviation security is Annex 17 of the Chicago Convention of the International Civil Aviation Organization (ICAO). This wide-ranging document provides the standard procedures and guidance for the civil aviation industry, on how to safeguard the industry against acts of unlawful interference. Annex 17 is amended regularly to address the evolving threat and it’s composed of five key sections, which are:
Although Annex 17 is the main ICAO Annex setting security standards and recommended practices, there are a number of other Annexes that influence the security operation of an airline or airport. Many are dealt with by those responsible for safety, the environment and the facilitation of the movement of passengers from point to point. The Annex also seeks to coordinate the activities of those involved in security programs.
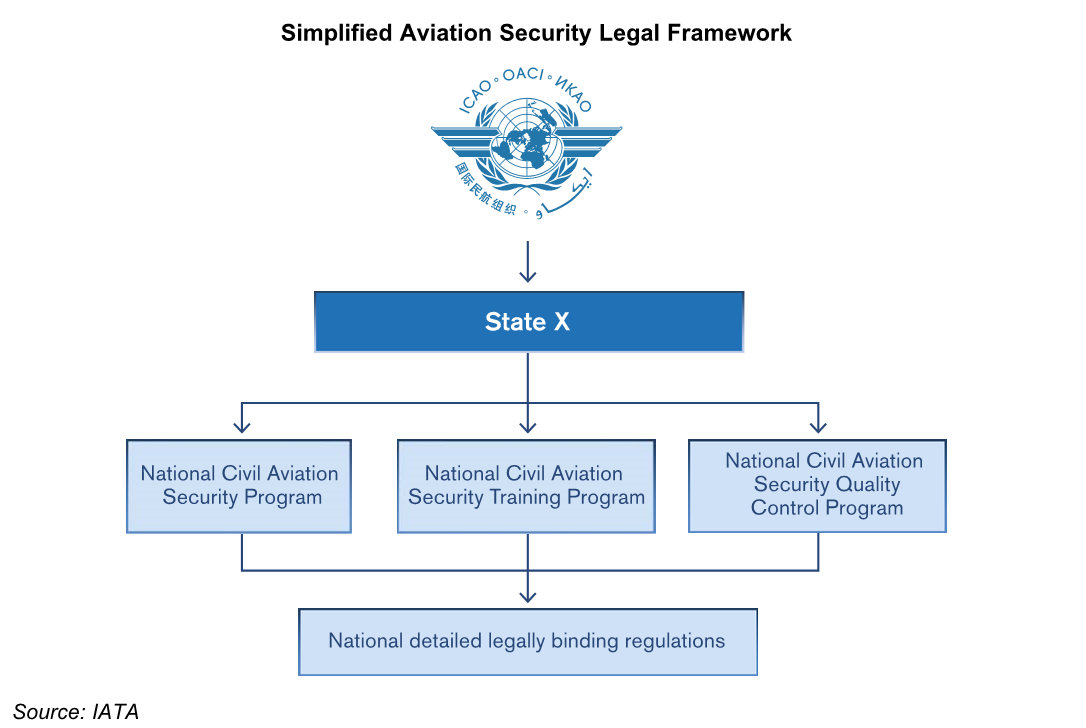
Overall, it is recognized that airline operators have a primary responsibility for protecting their passengers, assets and revenues. States need to ensure that airlines develop and implement complementary programs compatible with those of the States out of which they operate.
But it is important to remember that security is not only the responsibility of top-level management or the Head of Security. Security involves everyone and a positive security culture is essential in promoting and maintaining a secure environment. Positive reinforcement of correct security actions sends the message throughout an organization that management believes security to be a priority.
The ultimate goal is to enhance global security by implementing uniform security measures around the world, a goal that cannot be achieved without a solid commitment by all concerned.
Aviation security risks and threats evolve rapidly and manifest themselves in different forms. Some of the key threats can include:
It is clear risks cannot be totally avoided or eliminated. However, the goal is to reduce, as far as practicable and reasonable, the possibility of something going wrong and to reduce the potentially negative consequences that may arise as a result. There will always be factors beyond our control or beyond our knowledge such as new terrorist attack methodologies. As a result, everyone faces the inevitable challenge of balancing all the risk management variables to make maximum use of limited time, resources, personnel and funding.
A Security Management System (SeMS) provides an entity with a framework of operating principles and guidance which enable it to enhance security performance by proactively managing risks, threats, and areas where there are gaps and vulnerabilities which may have a negative impact on that performance.
SeMS is:
Take the five-minute SeMS Evaluation Test to learn more.
A SeMS also contributes to making security practices proactive, rather then relying on more traditional reactive and prescriptive procedures. It offers quantitative and qualitative benefits that can improve overall performance and communication within a company, as well as with State regulators. It enhances a company’s security culture, regulatory collaboration and resource utilization.
A robust SeMS will allow your organization to:
You can learn more about IATA's SeMS program and SeMS Competency Test by visiting the program's webpage.
A Security Management System (SeMS) enables security operators to streamline and optimize routine security and emergency preparedness. It will improve an organization’s efficiency and, with time, you will also often see cost reductions. Overall, five benefits you can expect after implementing a SeMS are:
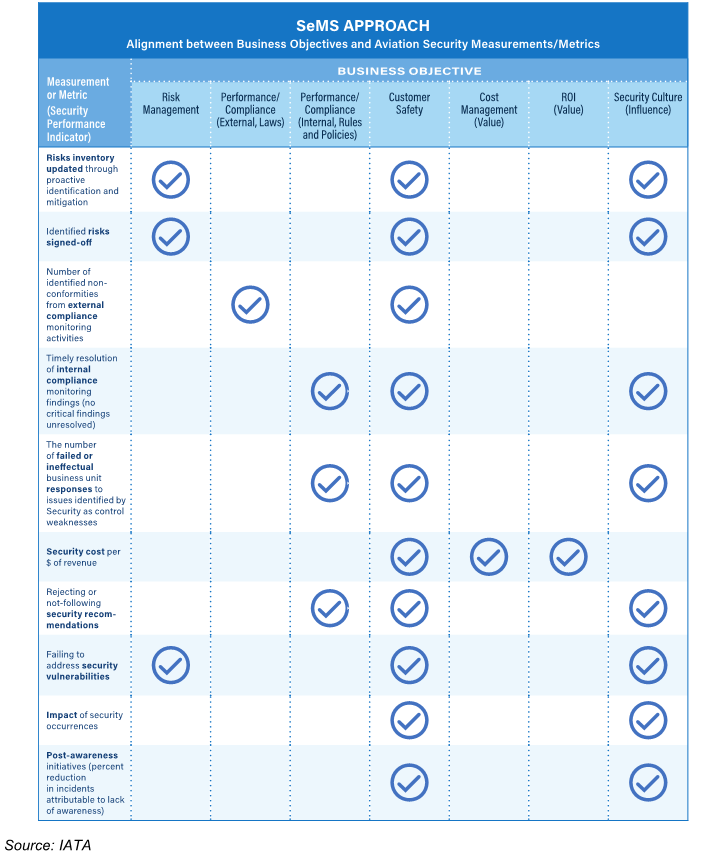
The performance of an organization’s SeMS is evaluated against five core components for an effective security culture. You can find them below with a few subitems. To view the full list along with the measures that should be taken at each step of an implementation and conformance phase, please view Chapter 6 of IATA’s Security Management System Manual.
You can learn the essentials of IATA’s SeMS initiative and how it can make your organization IOSA compliant by taking an IATA Training SeMS course. The course provides a structured approach to security process implementation in accordance with IATA Operational Safety Audit (IOSA) requirements. Thanks to the daily classroom exercises, you'll be able to begin building a performance-based SeMS that produces measurable and auditable results.
No matter the size, type or complexity, the top executives and senior management play a major role in determining a company’s commitment to security. When an organization decides that it will implement a SeMS in its operations, it is essential that a plan be drawn up. An implementation is complex and involves several entities within and outside the organization. In general, there are three stages (levels) of SeMS development:
A model SeMS implementation plan is included in Section 6.2 of IATA’s Security Management System Manual.
Take the five-minute SeMS Evaluation Test to learn more.
Security management is all about preventing incidents and keeping people and property safe. To do this we need to understand the associated risks and what could go wrong and, if something does go wrong, how bad will it be and how likely is it to occur.
Therefore, a risk assessment helps organizations to identify risks and threats, it also helps to understand which are the most significant and by being able to identify these different levels of risk, it will then help an organization prioritize these as not every risk can be addresses immediately due to organizational resource limitations. As a result, management needs to decide whether to accept given risks or take further action to reduce the risk to an acceptable level.
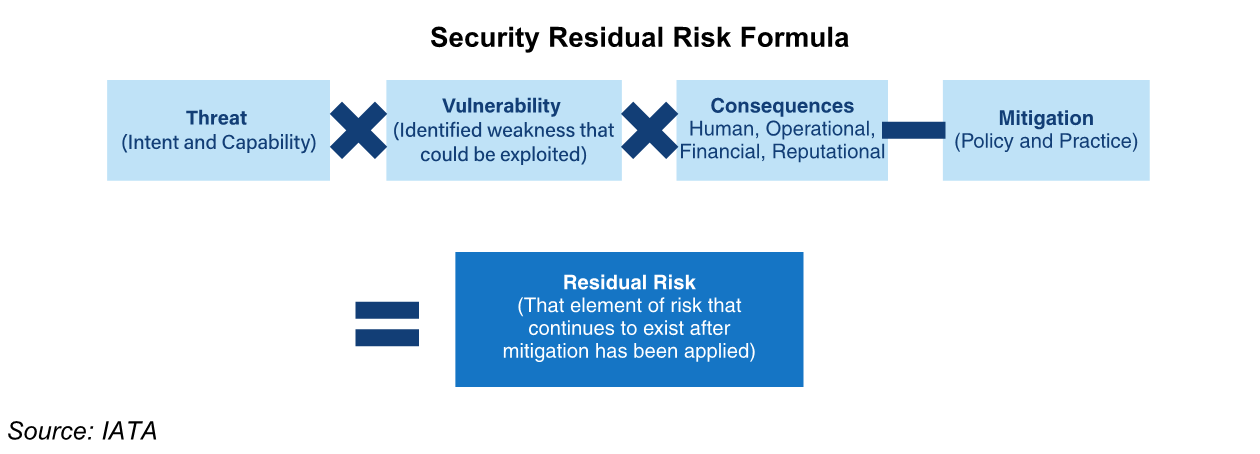
Risk initially stems from the result of a threat, real or perceived, and is typically a combination of two factors:
The threat, when combined with a vulnerability that is for instance a weakness that an attacker may be able to exploit such as a poor security perimeter, coupled with reasonable consequences that may result should a successful attack occur equals to risk.
From this calculation, one is required to factor in the degree of existing mitigation currently in place in terms of:
Having accounted for existing mitigation, the element of risk that remains after mitigation factors are taken into account is known as residual risk. Thus, the resulting calculation looks like this:
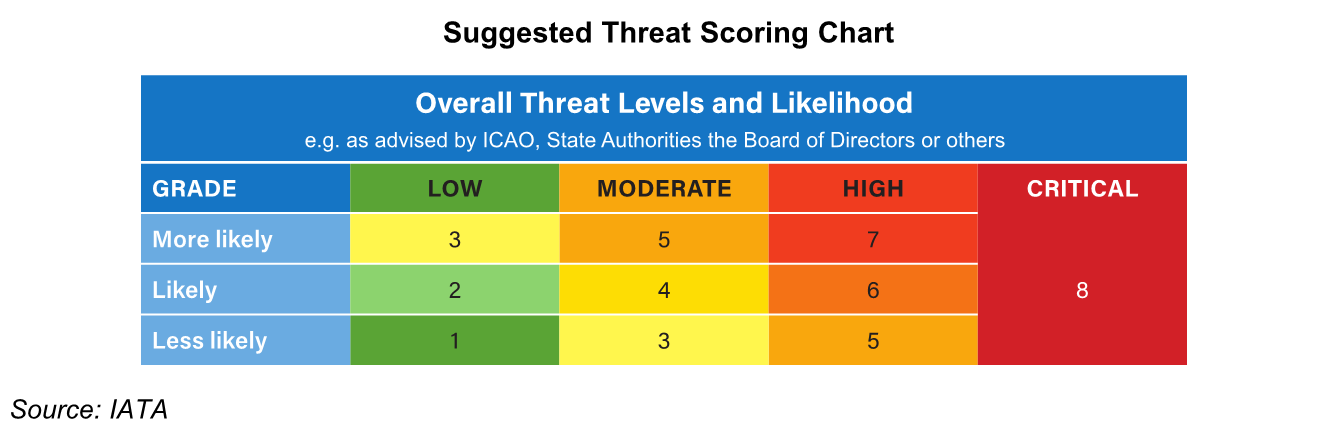
Tools such as the IATA’s threat assessment form and other guideline material can be found in Chapter 5 of IATA’s Security Management System Manual. For instance, the table below provides an example of a threat evaluation scoring chart.
Monitoring and periodic review should be a planned part of the risk management process, with the aim of monitoring the risk and the progress of mitigating actions. In addition to regular review, a change in the environment or organization might warrant an ad hoc review of the risks.
Therefore, whatever action is taken to control risks will require to be monitored so that we can make sure that it is working and effective. Tracking events can also help your security performance monitoring process as it’s all about learning from your past experiences. By providing high-quality, timely and detailed reports and assessments, feedback can then be easily shared to all relevant personnel to significantly improve security across your organization and industry.
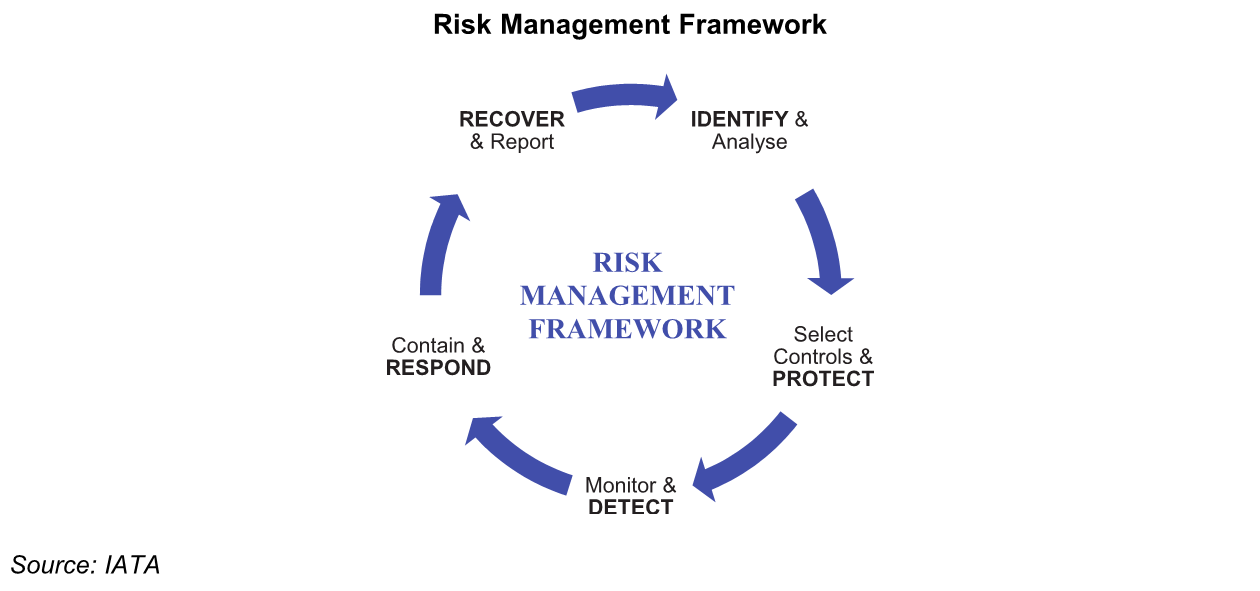
Recent events have caused a paradigm shift towards integrated risk management that considers safety, security and quality management in a cohesive manner. Equally, the need to have processes and procedures in the scope of emergency response planning seems indispensable.
The 1st edition of the Integrated Risk and Resilience Management Manual (IRRM) merges the previous Emergency Response Handbook (ERP) and the Integrated Risk Management Guide Manual (IRMGM), providing comprehensive guidance to any entity who is planning to fully integrate their risk management components and improve their emergency capabilities.
The IATA Integrated Risk and Resilience Management manual provides a step-by-step guide on how to manage exposure to risk in a smart and comprehensive manner, and is specifically designed for the aviation industry. However, even non-aviation entities may consider the model and processes presented. Beginning with a quick assessment of your current situation, the handbook will show you how to design a practical plan tailored to the needs of your organization.
Our trials of this methodology have produced extremely positive feedback from airlines and aviation companies around the globe. If you would like a more hands-on approach, you can take the Enterprise Risk Management for Aviation course offered by IATA Training. Over 4 days, you'll learn about the IATA IRM methodology and obtain the tools to implement a risk management process within your organization – from corporate risks to operational-related risks.
Passengers each year rely on the airline industry to get to their destination safely. Their safe passage is due to the tireless efforts of industry stakeholders. Working together, the industry has made aviation the safest form of travel. However, it is clear that risks cannot be totally avoided or eliminated, and that this impressive safety record is still subject to unlikely events. When an aircraft is diverted, disrupted or lost, there is a strong need for mechanisms to deal with the aftermath and recovery.
Therefore, an up-to-date Emergency Response Plan (ERP) can help and guide organizations to manage and recover from such events. This is outside of the Security Management System (SeMS), however it is a critical element in an organization’s structure and procedures.
The Integrated Risk and Resilience Management Manual is your one-stop shop with all the answers to help you deal with all aspects of emergency response preparedness. The handbook is developed by the IATA Emergency Response Planning Task Force, in collaboration with IATA member airlines.
This guidance material provides organizations with a wealth of critical information on the correct response to an incident. It’s designed to give you the necessary tools to create an ERP department from the ground up. You can also learn more about emergency planning and response by taking this IATA Training course.
The Security Management System (SeMS) Manual is all-encompassing guidance aiming to help all entities focus on essential aspects of security management. The aviation industry does not stand still, and neither should you. Strive for an efficient security management system and ensure the latest best practices are implemented in your organization.
The Manual covers a range of topics including security reporting, change management, accountabilities and responsibilities assignment, risk assessment, and quality assurance. You can learn more here.
Take the five-minute SeMS Evaluation Test to learn more.